Archive
From pass_file to Script Kiddies
This is a follow-up to my previous post. For background on this post, please read that post.
The botnet master behind the attacks described in the last post could be*:
- Romanian
- trancetears@yahoo.com, cezar179@yahoo.com and/or hotzu@hotzu.us
- Frequenting IRC (Undernet): Diemen.NL.EU.Undernet.org:6667
- Controlling a small botnet with IRC nickname fSs in channel #19
- Talking in these channels: #ls, #Work, #LinuxTeam, #Linux-Team, #Catalin, #112, #juno and #master
- Using small variations of the word “tears” for his/her handles and the handles of his/her bots
- (Probably) proxying his/her IRC connection through compromised hosts
- Using pre-packaged tools
*I don’t have any evidence indicating that this specific individual is the one attacking me (in fact it’s kind of a long shot), but I do have evidence that this individual is using a toolkit very similar to the one being used against me and that this individual is operating a botnet. You sacrifice privacy when you choose to run a botnet.
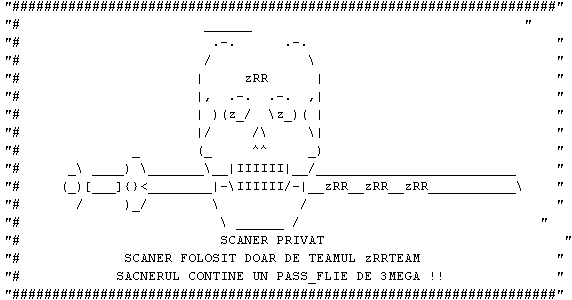
this is how you know they're legit. they have skulls and knives in their banners.
Gathering the info:
I’ve been running my modified sshd for a few days now, and as previously mentioned, I have a fairly lengthy log going already.
My original purpose for collecting full usernames & passwords tried against my server was to use those captured credentials to determine whether this dictionary attack was the work of a single group or the work of multiple groups. I set out determine which using the following observations:
- If there is a single group behind these attacks, it would make sense that they would synchronize this work amongst the attacking IPs, allowing the attack to evade simple IDS rules and avoid duplication of effort.
- If there are multiple parties behind these attacks, it would make sense that the same username/password combinations would be tried by different hosts, pointing to a lack of synchronization.
Let’s take a look at first two IPs in these logs:
- For about 8 minutes from 09/27/09 05:05:47 AM until 09/27/09 05:13:38 AM PST, 85.62.95.198 tried a list of 86 username / password combinations.
- For about 2 minutes from 09/27/09 07:06:10 AM until 09/27/09 07:08:03 AM PST, 190.82.64.149 tried the exact same username / password combinations in the exact same order.
- 85.62.95.198 made a request every 7 seconds and 190.82.64.149 made a request every 2 seconds, with very small clock drift.
- Using two hosts was almost certainly a duplication of effort (that is unless they were trying to determine the rate at which my ssh daemon would process logins…in which case they were just sloppy).
- Given the even spread of the attempts and the identical dictionaries, it’s not unreasonable to conclude that these two hosts are running the same attack software with a wait parameter changed.
So: one group (no synchronization of dictionaries between bots), or multiple groups (both using a common dictionary)?
In order to determine which, I needed more information on the toolkit in use here.
Warning: the URL below should not be visited without taking precautions. I use NoScript inside of a VM when looking at sites I know to be malicious. Whenever possible, I have notified the providers hosting this malicious software and have reported whatever is applicable to Google Safe Browsing.
I am a fan of full disclosure; I will be listing sites that are hosting malicious toolkits. Please do not make the mistake that blackhats find toolkits by reading whitehat blogs. They already know about and use these tools or could easily find them with simple Google searches (as I did). Exposure to real world attacks and toolkits is an important learning tool for anyone on the defensive. Not talking about them doesn’t help anyone.
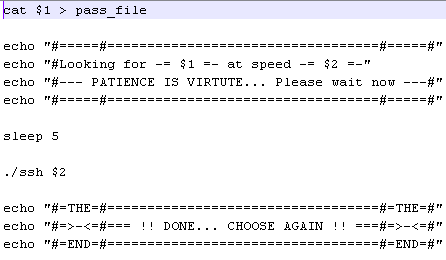
yeah - this is the entire script.
I took the odd-looking username/password combinations and ran some Google searches. The following is what I found with my first search. I’ve found much more than this, including more sophisticated attacks and full output (screenshots, keys pressed) from a keylogger, but going into that would be too much material for this post.
search term: mythtv vivafood
initial result: pass_file
host: f0rbidden.home.ro
notes: payload staging server; activity as recently as Sep. 13th
interesting files found on host:boo.tgz:
- Linux IRC bot
- c&c information
boodarwin.tgz:
- darwin: PPC Mach-O (OS X) IRC bot
- freebsd: FreeBSD IRC bot
- sendmail: Unix IRC bot
- pico (trojaned? are the attackers unfamiliar with vi?)
- help files and configuration for a popular botnet control program
- “random” IRC nicks, comments, away messages, insults, etc.
gosh.tgz:
- a bunch of things we’ve seen already
- ssh-scan, ss: ssh brute-forcer & tool; based on libssh-0.1
- pscan2: a port scanner
- a, go.sh: ssh-scan supporting scripts
- mfu.txt: a list of IPs serving SSH(?)
- vuln.txt: a file to hold successfully brute-forced hosts
- gen-pass.sh: combines a user list & password list into a single list
- secure.sh: checks if user is root, moves mail to s8 if user is root
psyBNC-2.3.2-7.tar.gz & psyDarwin.tgz:
- IRC bouncers (BNC). Allows the attackers to proxy their IRC connections through infected hosts.
sniff.tgz:
- a bunch of things we’ve seen already
- the bot master’s email address (found inside sniff/install)
liviu.tar (partially corrupted):
- a bunch of things we’ve seen already
- a PHP shell
- ps: trojan horse scanner
gosh.tgz is a Romanian(?) kit made a group identified as “TASE”.
scam, a file inside gosh.tgz, will email the following to hotzu@hotzu.us:
- output from /sbin/ifpconfig (IP address of bot)
- output from uptime (reliability of bot)
- /etc/issue (bot’s Linux distribution)
- /etc/passwd (valid users on bot)
- output from id (current user)
- output from df -h (disk space available on bot)
- output from pwd (working directory)
- current list of successfully brute-forced hosts
As previously stated, I’m not going to dissect the other malware staging servers I found as this would take too much time/space. I will, however, point out a few highlights that resulted from some simple Google searching with the usernames / passwords tried against me (you’re going to have to find these yourself):
- a complete PayPal phishing package (source code included)
- output from a keylogger (screenshots, captured credentials)
- possible source code for the ssh brute-force utility
- a rather odd place for a pass_file
- privilege escalation attempts (most likely successful, judging by the timestamps); very similar tools appear to be used post-escalation
- Conficker uses some of the same passwords that have been used against me
- valid* logins to SSH servers on compromised hosts
- the same toolkit (or slight variations thereof) on about a dozen hosts (hosting providers have been notified)
*Obviously I didn’t verify this.
At this point I know a lot about the tools most likely being run against me. But what about some more info on the attackers? IRC information was included in some malware kits…
I decided to look up the OP and see what other channels (s)he frequents. Almost all were Romanian chat channels, but #a1b2c3 looked interesting:
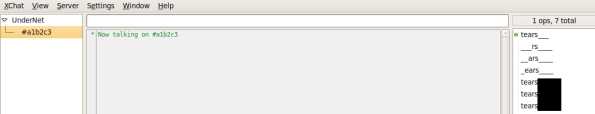
a very lonely c&c channel.
…as did #19:
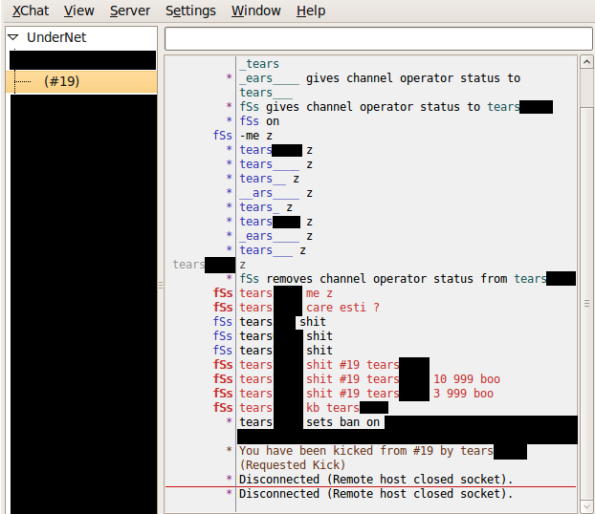
looks like (s)he figured me out. no more trolling c&c channels for me.
The #19 log is particularly interesting because you can clearly see fSs issue commands and expect a response. After I failed to respond correctly, was he actually asking me something or is all of this part of the “random” request/response/nickname/away message lists mentioned previously? Is everyone just reading from a script but me?
The command “shit” is an EnergyMech command. He told all his bots to ban me (shitlist me) for the next 999 days even if one of them tries to unban me. His reason for doing this is “boo”.
